The Great Data Heist
It's a digital world we live in, and with every click, every search, and every purchase, we're creating a digital trail of our lives. However, the question remains, who has access to our data, and what are they doing with it?
The truth is, our data is up for grabs, and it's being sold to the highest bidder. But what if there was a way to protect our data and identities, even from the organizations we have to trust?
The Weak Links in the Chain of Trust
We rely on organizations for everything, from internet services to electricity, but how can we be sure that they are trustworthy? Unfortunately, the answer is not so simple.
There are two major weak links in the chain of trust: the people we interact with at these organizations and their unsecured networks. These vulnerabilities can lead to our data being compromised by individuals, organizations, and even state actors who seek and pay for such information.
This is where zero-knowledge proofs have emerged as a potential solution.
But before we dig further, let’s outlay the technological progress in conducting transactions and exchanging information over the blockchain and the two major speed bumps hindering its mass adoption.
The Price of Progress: Privacy and Scalability Dilemma in Blockchain
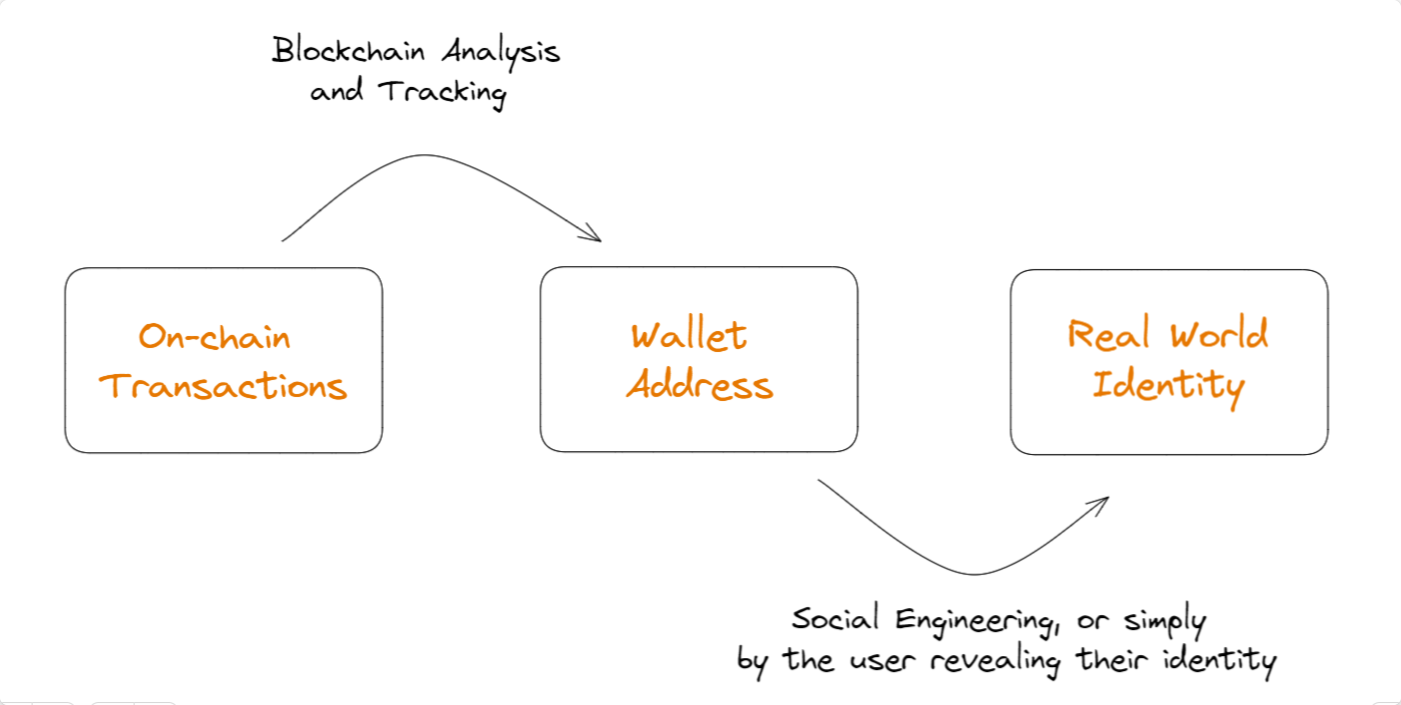
When it comes to privacy, blockchain is like a public diary; everything is recorded and visible to everyone, unless it's privacy-focused coins like ZCash and Monero. While this is great for transparency and proving the legitimacy of transactions, it also means that anyone can potentially connect the dots between your real-world identity and your on-chain transactions. Not cool.
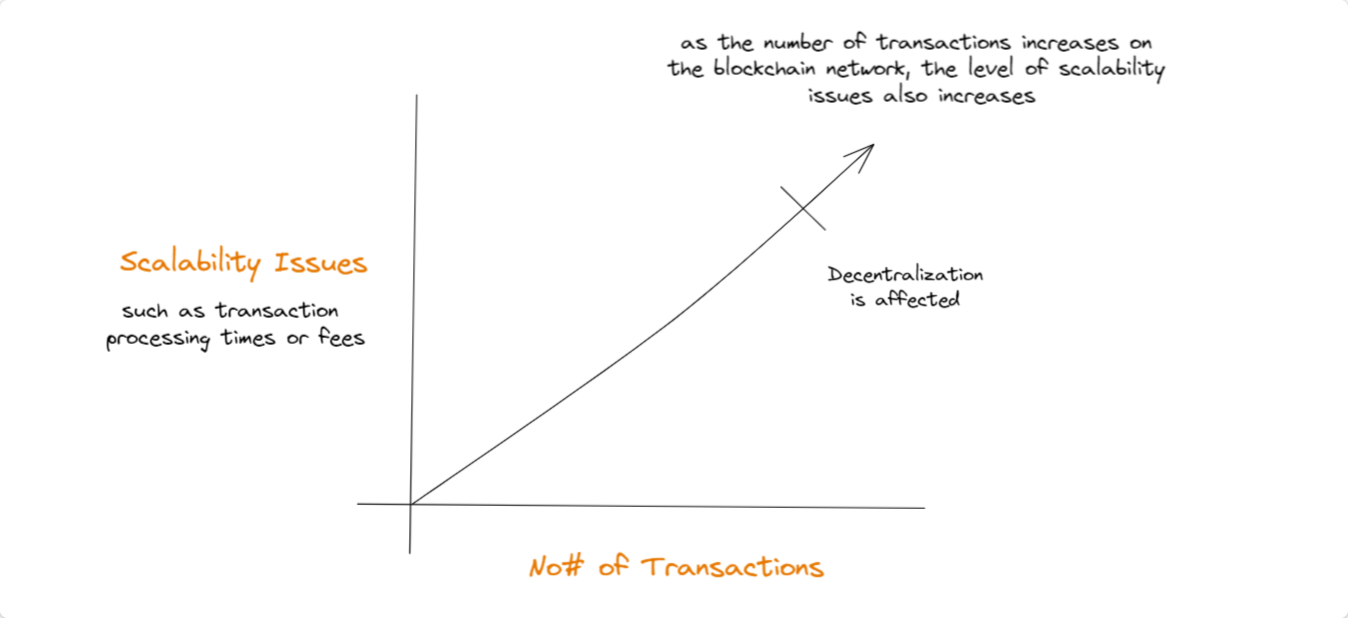
On the other hand, scalability has always been the talk of the town.
It’s like trying to fit too many people in a car. If too many transactions happen on the blockchain simultaneously, it can not handle the traffic without sacrificing decentralization. Therefore, we need to figure out how to make blockchain able to handle more transactions to make it accessible to more people.
Re-enter ZKPs
In the last article, we briefly explored zero-knowledge proofs and two of the most popular types of proof systems: ZK-SNARK and ZK-STARK. In this article, we will dive deeper into the specifics of ZK-STARK and how it can be used to solve the privacy and scalability dilemmas facing blockchain technology.
But before that, let’s outlay some of the underlying issues with ZK-SNARK.
Downside of ZK-SNARKs
Issue #1: The Trusted Setup Phase Can Be Compromised
Imagine an entity trying to bribe parties into setting up a ZK-SNARK system to share the setup parameters. If successful, this entity would be able to create false proofs and potentially change the outcome, leaving the door open for potential manipulation.
Note: Since the appearance of ZK-SNARKs, many follow-up works were intended to improve it, which do not follow a trusted setup. Read more!
Issue #2: Scalability
First, let's talk about arithmetic circuit complexity. This is a measure of how simple and efficient the code is that creates the zero-knowledge proof. In ZK-SNARKs, the complexity of the circuits is relative to their computational efficiency. Second, as the computation size increases, the communication needed to solve a problem also increases.
However, ZK-SNARKs have the advantage of a smaller proof size.
What about ZK-STARK?
zk-STARK stands for "Zero-Knowledge Scalable Transparent Argument of Knowledge." The name is a bit of a mouthful, so let's break it down!
— The Breakdown
ZK
zk, or "zero-knowledge," refers to the property of a proof system in which the prover can prove knowledge of a statement without revealing any information about the statement itself.
S: Scalable
The "S" in STARK stands for "Scalable," and is known to scale better than ZK-SNARKs.
The system is designed to handle large amounts of data and the proof generation and verification process is much faster. Meaning that the proof can handle large and complex statements.
It's efficient in computational and communication complexity and can scale up to handle more complex situations.
T: Transparent
The "T" in STARK stands for "transparent," meaning that the proof can be publicly verified without needing a trusted setup.
“A trusted setup is a procedure that involves more than one party. Its aim is to produce the standard parameters that a proof system or similar cryptographic protocols rely on. During this setup, random numbers (secrets) are generated, encrypted, used to generate the data, and then deleted to ensure the protocol remains foolproof. As the participants need to be trusted for the setup to fulfill its purpose, this process is called a trusted setup.”
In contrast, ZK-STARKs does not require a trusted setup.
Anyone with a copy of the verification algorithm and the statement can verify the proof. This allows the proof to be easily auditable, which can be useful in cases where regulatory compliance is a concern.
Transparency also allows for the verification to be performed in a decentralized manner, which can be useful in cases where a centralized authority is not desired or not feasible.
Finally, ARK: Argument of Knowledge
"ARK" in STARK stands for "argument of knowledge," which adds computational soundness to the system by ensuring that a bad actor cannot cheat the system without the knowledge to support their claim.
In simpler terms, ARK in STARKs is a way to ensure the security and accuracy of the information used in the system, similar to ZK-SNARKs. However, instead of using the same ZK-SNARKs, STARKs use a different approach involving hash functions.
This is designed to be more resistant to cheating, eliminating the need for an additional step called "trusted setup" that is required in ZK-SNARKs.
The upside
One of the main advantages of ZK-STARKs is their transparency. ZK-STARKs are transparent and do not require this trust. This is particularly important in the cryptocurrency community, where trust is often lacking.
Another advantage of ZK-STARKs is that they are post-quantum systems, meaning that they are not vulnerable to advances in quantum computing. With no external trusted setup phase, publicly verifiable randomness and resistance to quantum computing attacks, you can trust that your data is safe and secure.
In contrast, ZK-SNARKs are based on elliptic-curve cryptography, which is susceptible to quantum computing advances.
Building Trust with ZK-STARKs: Applications in High-Stakes Industries
There are many areas where ZK-STARKs can be implemented to enhance trust, especially in industries where there are large incentives to cheat. For example, in the financial industry, ZK-STARKs can be used to verify the authenticity of financial transactions without revealing sensitive information. This can prevent fraud and increase trust in the system.
In the voting industry, ZK-STARKs can be used to ensure the integrity of the voting process by allowing for the verification of votes without revealing how a voter voted. This can prevent voter manipulation and increase trust in the democratic process.
In the healthcare industry, ZK-STARKs can verify medical records' authenticity without revealing sensitive information. This can prevent medical fraud and increase trust in the healthcare system.
In conclusion, ZK-STARKs offer a valuable solution for creating trust in industries where personal data needs to be protected, and the integrity of transactions must be maintained. Its scalability, transparency, and current quantum resistance make it a reliable technology that can increase trust in various systems.
